
What is Search Engine Optimization (SEO)?
Search engine optimization (SEO) is one of the most important aspects of digital marketing. It focuses on getting your website to appear at the top of search engine rankings, so that[…]
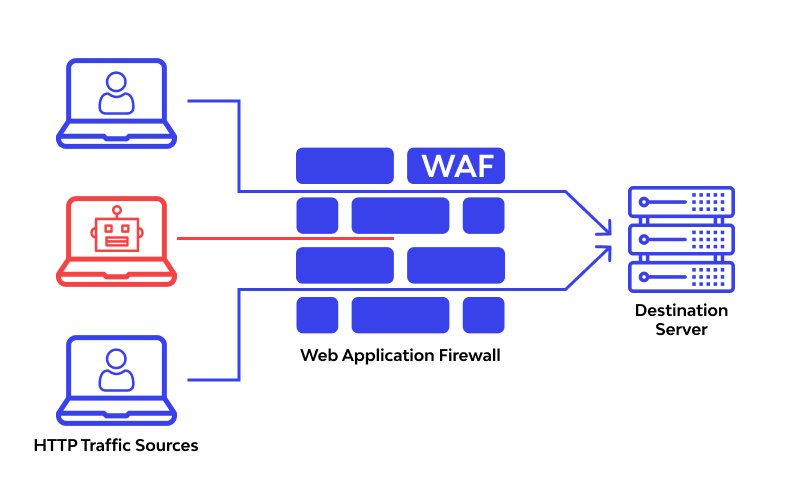
What is a WAF (Web Application Firewall)?
A Web Application Firewall (WAF) is an important tool for any website owner. It provides a layer of security that helps protect against malicious attacks such as SQL injection, cross-site scripting,[…]

What is HTTP Strict Transport Security (HSTS)?
Have you ever heard of HSTS, and wondered what it is? HSTS stands for HTTP Strict Transport Security, and is a web security protocol that helps protect websites from various attacks[…]

What is Typo-squatting?
Typosquatting is a type of cyber attack where a malicious actor registers domain names that are similar to popular websites, hoping to trick users into visiting their malicious sites. In this[…]

What is DMARC?
Email security is a top priority for businesses today, and DMARC is a key element in ensuring that your emails are properly protected. DMARC, or Domain-based Message Authentication, Reporting & Conformance,[…]

What is DKIM (DomainKeys Identified Mail)?
DKIM (DomainKeys Identified Mail) is an email security standard designed to help protect businesses and end users from malicious emails. It works by using a digital signature to authenticate emails sent[…]

What is SPF (Sender Policy Framework) in email security?
Email security is one of the most important aspects of keeping your data and information safe. One of the key components of email security is SPF (Sender Policy Framework). SPF is[…]
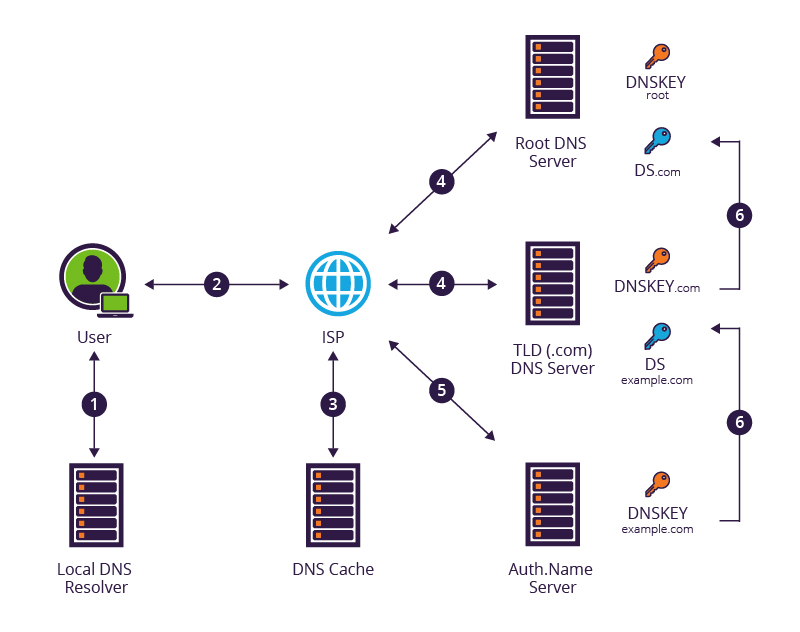
What is DNSSEC?
In today’s digital world, we rely on the Domain Name System (DNS) to connect us to websites, applications, and services. Unfortunately, DNS is not as secure as it could be, making[…]

Mobile device security and it’s importance
As mobile device use becomes increasingly prevalent, it is important to understand the implications of inadequate mobile device security. In a world where digital security is becoming more and more important,[…]

What is PoLP (Principal of Least Privilege)?
The Principle of Least Privilege (PoLP) is an important security concept that is used to limit the potential damage caused by malicious actors. It is based on the idea that an[…]
