
The importance of physical IT security
Physical IT security is a necessary but often overlooked element of a comprehensive cybersecurity strategy. While most organizations focus on defending their networks from cyber threats, physical IT security is just[…]
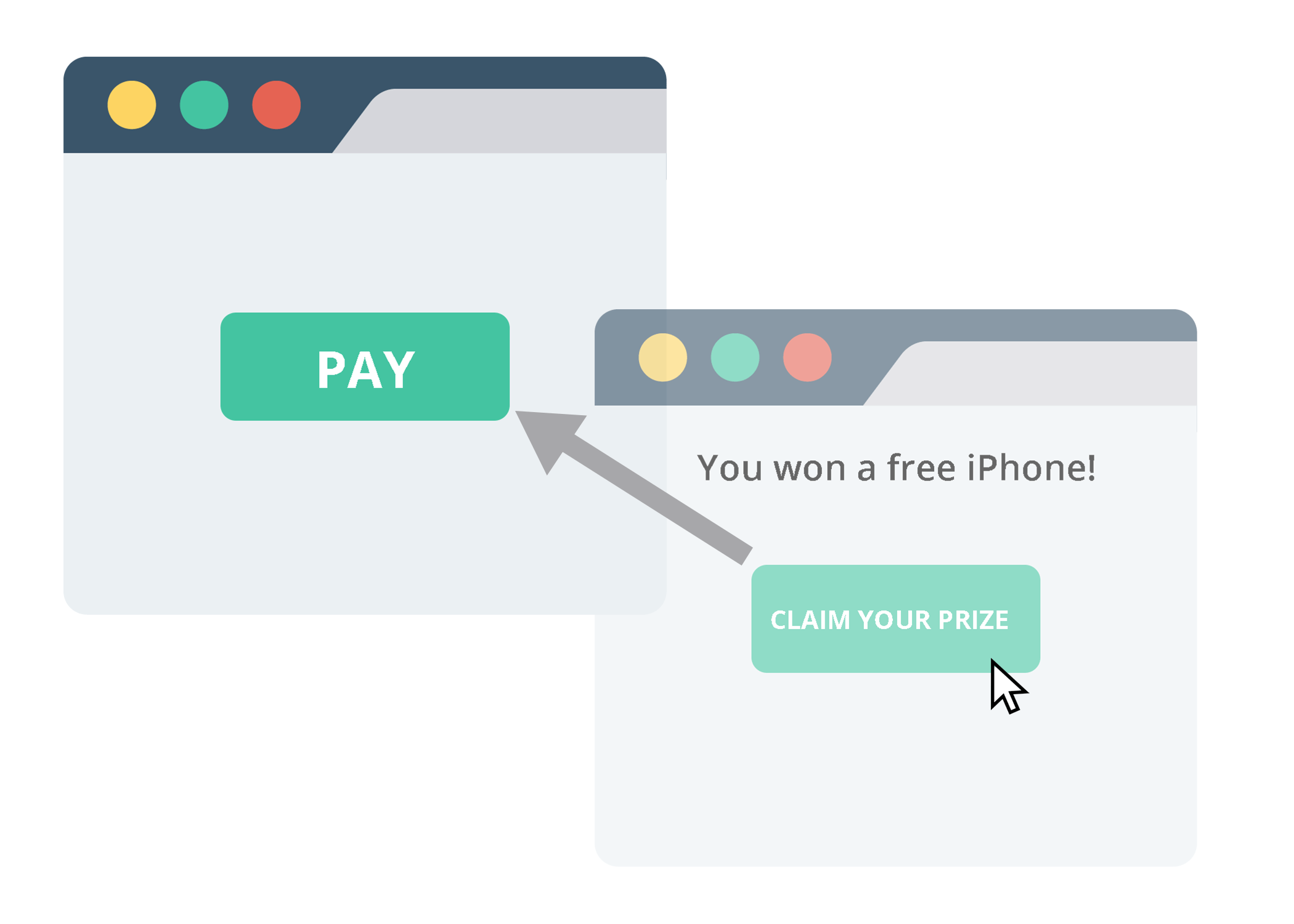
What is click-jacking and how to protect against it?
Click-jacking is a serious security risk that affects millions of internet users every year. In its most basic form, click-jacking is a technique used by malicious actors to deceive a user[…]

Phishing Scams: How to Protect Yourself and Your Business
Phishing scams are one of the most common and dangerous types of cyber threats facing individuals and organizations today. These scams involve tricking people into providing sensitive information, such as login[…]

Why are Open-Source initiatives so important?
An open-source initiative is a project or program in which the source code of a program is made available to users and developers for free. This allows users and developers to[…]

What is password entropy and why does it matter?
Password entropy is a measure of how secure a password is against guessing. It takes into account the length, complexity, and randomness of the password to calculate the likelihood that an[…]

Why is SSL (TLS) important for the modern web?
Over the past few years, the importance of SSL/TLS has grown exponentially in the web world. SSL/TLS has become an essential part of any website’s security, and it is important to[…]

Why do we need MFA?
As the world of technology and the internet continues to evolve and become increasingly sophisticated, the need to secure our personal and professional data has become more important than ever. Multi–factor[…]
